Exploring Docker Networking: Introduction to Network Drivers, Bridge Networks, Overlay Networks, and More
June 27, 2023 Leave a comment
Docker networking plays a crucial role in connecting containers and enabling communication between them. Understanding the intricacies of Docker networking is essential for building scalable and distributed applications. In this in-depth guide, we will delve into various aspects of Docker networking, covering topics such as bridge networks, overlay networks, network drivers, IPAM drivers, exposing containers externally, troubleshooting, and more. By the end of this article, you’ll have a solid understanding of Docker networking concepts and be able to configure and manage networks effectively.
Docker networking enables containers to communicate with each other and the outside world. By default, Docker uses a virtual network that allows containers to communicate using IP addresses. However, Docker provides various network drivers to create different types of networks based on specific requirements.
Bridge Networks: Connecting Containers on a Single Host
Bridge networks are used to enable communication between containers running on the same Docker host. Each container attached to a bridge network can communicate with other containers on the same network using IP addresses.
Default Bridge Network Driver
Docker provides a default bridge network driver that allows containers to communicate with each other by their container names. The default bridge network is created automatically when Docker is installed.
Creating Custom Bridge Networks:
To create a custom bridge network, you can use the docker network create command. Here’s an example:
sudo docker network create mynetwork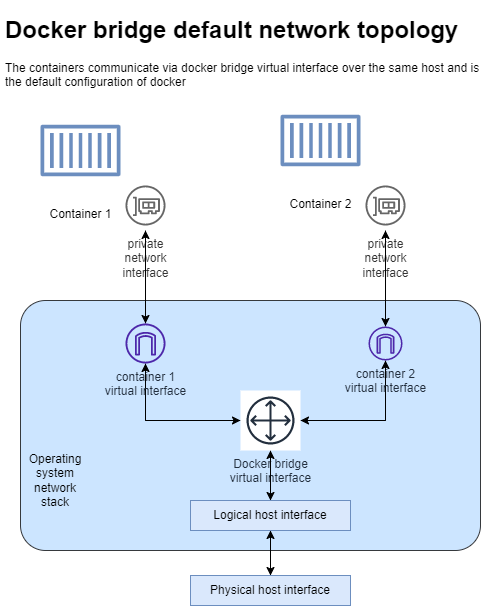
Let’s walk through the steps of how network communication happens in this scenario:
- Bridge Network Creation: When Docker is installed, a default bridge network named
bridgeis created automatically. This bridge network provides a virtual network environment for containers running on the same host to communicate with each other. - Container Attachment to the Bridge Network: To enable network communication, both containers need to be attached to the bridge network. This can be achieved during container creation or by connecting existing containers to the network using the
docker network connectcommand. - IP Address Assignment: Once the containers are attached to the bridge network, Docker assigns an IP address to each container within the bridge network subnet. These IP addresses are internal to the bridge network and are used for container-to-container communication.
- DNS Resolution: By default, Docker provides DNS resolution between containers within the same bridge network. Each container is assigned a hostname based on its container name, which allows easy communication using hostname-based addressing.
- Network Communication: With the containers attached to the bridge network and assigned IP addresses, they can communicate with each other using standard networking protocols. Containers can use the assigned IP addresses or hostnames to establish connections and exchange data.
- Port Mapping: If a container exposes ports, other containers or applications outside the bridge network can access those services through port mapping. Port mapping allows incoming network traffic to be directed to the specific container and port it is bound to.
- Network Isolation: The bridge network provides network isolation for containers. Containers connected to the bridge network can communicate with each other, but they are isolated from the host network and other networks by default. This isolation enhances security and prevents conflicts with the host network.
Overlay Networks: Networking Containers Across Multiple Hosts
Overlay networks allow containers to communicate with each other across multiple Docker hosts. This is particularly useful in Docker Swarm mode, where containers are distributed across a cluster of Docker hosts.
Automatic Configuration in Docker Swarm
In Docker Swarm mode, overlay networks are automatically created and managed by Docker. When you deploy a service in Swarm mode, Docker configures the necessary overlay network for the service to communicate with other containers.
Creating an Overlay Network:
To manually create an overlay network, you can use the docker network create command with the --driver overlay option. Here’s an example:
sudo docker network create --driver overlay myoverlayMACVLAN Network Driver: Directly Connecting Containers to Host Interfaces
The MACVLAN network driver allows containers to interface directly with host interfaces, bypassing the virtual Docker bridge. This provides better performance and allows containers to have their own MAC address.
Similarities to the Bridge Driver
The MACVLAN driver has similarities to the bridge driver in terms of networking capabilities. However, instead of using a virtual bridge, MACVLAN maps a container’s virtual interface to a physical interface on the host.
None Network Driver: Isolating Containers from Network Access
The None network driver isolates containers from the network, preventing them from accessing external networks or being accessed by other containers. This can be useful for creating isolated environments or running containers with limited network access.
Use Cases and Considerations:
The None network driver can be utilized in scenarios where network isolation is required, such as running containers for internal testing or creating secure sandboxed environments. However, it’s important to note that containers using the None network driver will not have network connectivity.
Exposing Containers Externally
Publishing Ports: Host vs. Ingress Modes:
Docker provides different ways to expose container ports to the external network. The two main modes are host mode and ingress mode.
- Host mode: In host mode, the container uses the host’s network stack directly, allowing it to bind to ports on the host. This means that multiple containers cannot bind to the same port on the host.
- Ingress mode: Ingress mode is used in Docker Swarm mode to expose containers externally. In this mode, Docker automatically routes incoming traffic to the appropriate container in the swarm.
Network Troubleshooting and Diagnostic Commands
When encountering network-related issues with Docker, several tools can aid in troubleshooting. These include ping, nslookup, netstat, and tcpdump.
When troubleshooting network issues in Docker, you can use the following commands:
docker network ls: Lists all the available networks.docker network inspect <network_name>: Provides detailed information about a specific network.docker network connect <network_name> <container_name>: Connects a container to a specific network.docker network disconnect <network_name> <container_name>: Disconnects a container from a specific network.
Common network issues in Docker can include container connectivity problems, DNS resolution failures, or incorrect network configurations. Troubleshooting techniques involve inspecting network settings, verifying DNS configurations, and checking firewall rules.
Configuring Docker to Use External DNS
By default, Docker uses its internal DNS resolution mechanism. However, there may be cases where you need to configure Docker to use an external DNS server.
To configure Docker to use an external DNS server, you can modify the Docker daemon configuration file and specify the desired DNS server. The specific steps may vary depending on your operating system and Docker version.
Conclusion:
Docker networking is a critical aspect of containerized application development. In this comprehensive guide, we explored various networking concepts, including bridge networks, overlay networks, network drivers, exposing containers externally, troubleshooting, and configuring external DNS. By understanding these concepts and employing the appropriate networking techniques, you can design and manage Docker networks effectively, ensuring seamless communication between containers and building resilient distributed systems.


